Web
Leveraging AI for Personalized User Experiences in Web Applications
Remember the days of one-size-fits-all websites? They felt a bit like getting a generic birthday card – nice gesture, but not exactly personal. Today, users expect more. They crave experiences tailored specifically to them. Enter Artificial Intelligence (AI).
AI isn’t just sci-fi anymore. It’s the engine driving truly personalized user experiences in modern web applications. It transforms generic interactions into relevant, engaging journeys.
Why does this matter? Because personalization isn’t just a nice-to-have; it’s a business imperative.
The Power of Personal Touch (Even Digitally)
Generic experiences are forgettable. Personalized ones stick. When a web application understands and anticipates a user’s needs, magic happens:
- Engagement Soars: Users spend more time interacting when content and features resonate.
- Conversions Climb: Relevant recommendations and tailored pathways lead users towards desired actions.
- Loyalty Builds: Feeling understood fosters a stronger connection between the user and the brand.
Think about it: you’re more likely to return to a coffee shop that remembers your usual order. AI helps your web application do the digital equivalent. Ignoring personalization is like serving everyone plain vanilla – safe, but boring.
How AI Weaves the Personalization Magic
AI achieves this through several key capabilities:
-
Mastering the Data Deluge: AI algorithms excel at processing vast amounts of user data – browsing history, click patterns, demographics, past purchases, time spent on pages. This isn’t just collecting data; it’s understanding the story behind it. Of course, handling this data securely and efficiently requires a solid foundation. Reliable Cloud Services are crucial for managing the infrastructure needed for AI-driven insights.
-
Predicting the Future (Sort Of): Based on historical data and patterns, AI uses predictive analytics to anticipate what a user might want or do next. It can forecast preferences, potential churn, or the likelihood of conversion. It’s less crystal ball, more highly educated guess.
-
Smarter Recommendations: This is the classic example. Think Netflix suggesting shows or Amazon recommending products. AI analyzes user behavior and compares it to similar users to suggest relevant content, products, or features within your web application. This keeps users engaged and helps them discover value they might otherwise miss.
-
Dynamic Interfaces: Why should everyone see the exact same layout? AI can subtly adjust the user interface (UI) or user experience (UX) based on individual preferences or behavior. This could mean highlighting certain features, rearranging modules, or simplifying navigation for specific user segments. Building such adaptable interfaces requires skilled developers, whether for complex Web Application Development or creating flexible themes within platforms like WordPress (WordPress Development Services).
-
Personalized Search & Discovery: Generic internal search results can be frustrating. AI can personalize search results within your application, prioritizing information most relevant to the individual user based on their past interactions and profile. This mirrors the principles of good external Search Engine Optimization, focusing on delivering the most relevant results quickly.
-
Intelligent Conversations: AI-powered chatbots and virtual assistants offer instant, personalized support 24/7. They can access user history to provide relevant answers, guide users through processes, and even handle transactions – all in a conversational manner. Need a chatbot that truly understands your customers? Explore Custom Conversational AI Agents.
Personalization in Action
Let’s look at some examples:
- E-commerce: Suggesting complementary products (“Customers who bought this also liked…”), personalized promotions, or even dynamically adjusting product displays based on browsing history.
- Content Platforms: Curating news feeds, recommending articles or videos based on reading/viewing habits. Many successful content sites rely on robust platforms and custom features, often built through expert WordPress Development Services.
- SaaS Applications: Offering personalized onboarding flows, highlighting relevant features based on user roles or usage patterns, and providing proactive tips. This level of sophistication is a hallmark of well-executed Web Application Development.
- Mobile Experiences: Extending personalization seamlessly to handheld devices, using location data (with permission!) or app usage patterns for tailored notifications and content. This requires dedicated focus during Mobile Application Development.
Ready to Get Personal?
Implementing AI personalization doesn’t have to be an overwhelming overhaul.
- Start Focused: Identify 1-2 key areas where personalization could have the biggest impact on your user experience and business goals.
- Data is Your Foundation: Ensure you have clean, accessible, and ethically sourced user data. Robust data management, often supported by scalable Cloud Services, is non-negotiable.
- Choose the Right Tools & Partners: Select AI tools and platforms that fit your needs and technical capabilities. Often, integrating these tools effectively requires expertise in Web Application Development or specific AI integrations.
- Iterate and Refine: AI personalization is not a set-it-and-forget-it solution. Continuously monitor results, gather feedback, and refine your algorithms.
The Future is Tailored
AI-driven personalization is rapidly shifting from a competitive advantage to a baseline expectation. Users increasingly expect digital experiences that understand and adapt to them. By leveraging AI, you can move beyond generic interactions and build web applications that feel intuitive, relevant, and genuinely helpful.
Ready to explore how AI can transform your user experience? Whether it’s building intelligent web applications, deploying custom AI agents, or ensuring your cloud infrastructure is ready, we can help.
Why Regular Security Audits are Crucial for Your Web Application
Your web application is a vital business asset. It might serve as your storefront, your primary service delivery platform, or even the core of your daily operations. But a critical question looms: Is it truly secure?
In today’s constantly evolving digital landscape, simply assuming safety is a dangerous gamble. Cyber threats are becoming increasingly sophisticated. Consequently, regular security audits are no longer an optional best practice; they are essential, fundamental maintenance for your digital infrastructure.
Think of it like servicing your car. You wouldn’t wait for a major breakdown before getting an oil change or checking the brakes, right? Security audits function as the necessary, proactive check-ups your web application requires to stay healthy and protected.
What Exactly Constitutes a Security Audit?
A web application security audit is a systematic and comprehensive evaluation of your application’s defenses. This process involves rigorous testing and analysis specifically designed to uncover vulnerabilities that malicious actors could potentially exploit.
Crucially, this goes far beyond merely running an automated scanner. A thorough audit typically combines powerful automated tools with meticulous manual testing performed by experienced security experts. These professionals will probe and test your application, mimicking the techniques a real attacker would use – with the critical difference being that they report their findings back to you rather than stealing your data or disrupting your services.
Identify Weaknesses Before Cybercriminals Do
The digital threat landscape is dynamic; new vulnerabilities are discovered every day. What was considered secure yesterday could potentially be vulnerable today. Cybercriminals are constantly scanning for easy targets to exploit.
Regular audits empower you to identify common and emerging weaknesses, such as:
- SQL Injection: Manipulating your database through input fields.
- Cross-Site Scripting (XSS): Injecting malicious scripts into web pages viewed by other users.
- Insecure Authentication/Authorization: Flaws in how users log in and what actions they are allowed to perform.
- Sensitive Data Exposure: Unintentional leakage or inadequate protection of confidential information.
- Security Misconfigurations: Errors in server, network, or application settings that create vulnerabilities.
Finding these flaws before an attacker discovers them is the primary objective. It’s analogous to diligently checking the locks on your doors before a burglar attempts to gain entry. Neglecting security audits? That’s akin to leaving your door wide open with a sign reading ‘Free Data Inside.’ Less appealing than free cookies, and infinitely more damaging.
Safeguard Your Most Valuable Asset: Data
Your web application likely handles sensitive and confidential information, ranging from customer details and financial data to proprietary business logic. A data breach involving this information can have catastrophic consequences.
Audits play a vital role in verifying that your data protection measures are robust and effective. This includes assessing encryption (both data in transit and data at rest), scrutinizing access controls, and reviewing overall data handling procedures.
Failure to protect data adequately can result in substantial fines under regulations like GDPR or CCPA, alongside causing irreparable damage to your brand’s reputation.
Preserve Customer Trust and Enhance Brand Reputation
Trust is painstakingly earned and alarmingly easy to lose. A security breach can erode customer confidence faster and more severely than almost any other incident.
Would you willingly entrust your sensitive information to a business that has demonstrated an inability to protect data? Most likely not.
Demonstrating a proactive commitment to security through regular audits significantly builds and maintains trust. It signals to customers, partners, and stakeholders that you prioritize their security and privacy. A secure application is not merely a technical feature; it’s a fundamental cornerstone of your brand’s integrity and reliability. This positive reputation can also indirectly boost your online visibility, complementing efforts like Search Engine Optimization (SEO).
Ensure Essential Business Continuity
Imagine a scenario where your web application is suddenly rendered inoperable due to a cyberattack. What is the potential cost to your business?
- Significant loss of revenue.
- Severe decrease in productivity.
- High emergency recovery expenses.
- Potential legal fees and settlements.
Security incidents have the potential to halt your operations entirely. Audits help prevent devastating attacks like Denial of Service (DoS) or ransomware that can cripple your business functions. Keeping your application running smoothly and reliably is absolutely paramount.
Meet Compliance and Regulatory Obligations
Numerous industries operate under specific security standards and regulatory frameworks (e.g., HIPAA for healthcare, PCI-DSS for payment card processing). Regular security audits are frequently a mandatory requirement for maintaining compliance with these standards.
Failing an audit or neglecting to conduct them altogether can lead to severe penalties, loss of essential certifications, and significant legal troubles. Audits provide the necessary documentation and evidence to demonstrate due diligence and adherence to required standards.
Optimize Performance and Improve Code Quality
In some instances, security vulnerabilities can originate from inefficient, outdated, or poorly written code. The systematic process of identifying and remediating these security flaws often naturally leads to cleaner, more optimized code.
This can result in a tangible improvement in your application’s performance and overall stability. Secure coding practices, which are a significant focus during our Web Application Development process, frequently go hand-in-hand with developing efficient and robust code.
Secure Your Underlying Infrastructure, Especially in Cloud Environments
Your application does not exist in isolation. It operates on servers, potentially within complex cloud computing environments. A comprehensive audit must extend to assessing the security posture of this underlying infrastructure.
Are server configurations properly hardened? Are network security rules appropriately defined and enforced? Is access to infrastructure components properly managed and monitored? This is especially critical if you leverage cloud platforms; ensuring these environments are securely configured and maintained is vital. Our Cloud Services expertise focuses on designing, setting up, and managing secure and resilient cloud infrastructure.
Don’t Overlook Third-Party Integrations (Including AI!)
Modern web applications are rarely monolithic; they typically integrate with a variety of third-party services, external APIs, and increasingly, advanced AI systems. Each point of integration represents a potential entry point that attackers could exploit.
Security audits must thoroughly examine these external connections. Are APIs properly secured and authenticated? Is data exchanged securely between your application and external services? If you are enhancing user experience or automating processes with tools like our Custom Conversational AI Agents, ensuring their secure integration is absolutely vital.
What About Companion Mobile Applications?
If your web application has a complementary mobile app, its security is equally critical. Mobile applications have their own unique set of vulnerabilities related to device storage, secure API communication, and platform-specific security considerations.
Achieving comprehensive security requires auditing both the web application front-end and any associated mobile applications. While our Mobile Application Development process incorporates security best practices from the initial design phase, regular audits remain crucial post-launch.
Specific Platforms Demand Specific Attention (Like WordPress)
Are you utilizing a popular Content Management System like WordPress? This platform has a vast ecosystem of themes and plugins, each of which can potentially introduce new vulnerabilities.
Audits for WordPress-based sites require specialized expertise to meticulously check core file integrity, theme and plugin security, user role configurations, and common WordPress-specific attack vectors. If your site is built on WordPress, specialized and regular audits are essential. Our WordPress Development Services team possesses the specific knowledge needed to address these nuances.
How Frequently Should You Conduct Audits?
There is no single, universally applicable answer, but the principle of “regularly” is paramount. When determining frequency, consider the following factors:
- Risk Level: High-traffic e-commerce platforms handling sensitive financial data require more frequent and in-depth audits than simple brochure websites.
- Compliance Requirements: Specific industry regulations may mandate a minimum audit frequency (e.g., annually for PCI-DSS).
- Application Changes: Conduct audits after significant application updates, major feature releases, or substantial changes to your underlying infrastructure.
- General Best Practice: Annually is a common baseline for many applications, with quarterly or bi-annual audits recommended for applications handling higher-risk data or critical business processes.
Invest in Security, Don’t Just React to Disaster
Security audits should not be viewed as a mere expense; they are a critical investment in the stability, reputation, and long-term future of your business. Proactive security measures are invariably less costly and significantly less stressful than attempting to recover from the aftermath of a major security breach.
Do not wait for a security incident to occur and force your hand. Make regular, systematic security audits a standard and integral part of your web application’s lifecycle. It is the intelligent, responsible, and ultimately more cost-effective way to protect your valuable digital assets and maintain the trust of the customers who rely on you with their data.
The case against shared hosting
Combating Robocalls with Robo-Bouncer
Case Study: Introducing the RoboBouncer – AI-Powered Call Screening
In this case study, we demonstrate how we bring our internet and programming skills to traditional telecommunications through a project we’ve dubbed the RoboBouncer.
The RoboBouncer is an intelligent bot designed to screen your incoming voice phone calls. When a call comes in, the system asks the caller to state their name and records it. It then places the caller on hold while simultaneously making an outbound call to your personal phone number. You are played the recorded name, and the system provides you with a clear option to either accept or reject the call.
With full programmatic control over call handling logic, the possibilities that the internet brings to traditional telephony are virtually endless. Beyond the RoboBouncer, we have experience setting up sophisticated phone systems, including:
- Interactive Voice Response (IVR) systems (e.g., company directories).
- Advanced lead transfer systems.
- High-volume outbound calling solutions.
To personally test out the RoboBouncer service, you are welcome to call our dedicated phone number: (949) 446-1716.
Following popular demand, we have also developed a commercial version that automates the deployment and setup of your own RoboBouncer instance. Click here to create your own RoboBouncer easily.
For those who are technically inclined, we have made the code and detailed information available in our BitBucket repository.
Creating a telephone call screening service using Twilio
This project demonstrates the creation of a call screening service utilizing the Twilio platform.
The Call Flow:
- Caller calls your Twilio Number: The system (the “agent”) answers and prompts the caller to speak their name, which is then recorded. The caller is subsequently placed in a queue (representing the “Inbound Call”).
- Outbound Call to You: Using the Twilio REST API, the system initiates an outbound call from your Twilio Number to your designated personal phone number.
- Playback and Options: When you answer, the recorded name of the caller is played back to you. You are then presented with the following options:
- Press 1 (DTMF) or Say “Accept” (SpeechResult): This action uses Twilio’s Dial verb to connect your phone to the caller who is waiting in the queue.
- Press 2 (DTMF) or Say “Reject” (SpeechResult): Using the REST API, the system notifies the waiting caller (e.g., with a message like “The person you are trying to reach is unavailable”) and then ends the call for both parties (hangs up on the caller in the queue and hangs up on your outbound call).
Technical Details:
- Uses the TWIML API and the Twilio Voice API PHP SDK.
- Utilizes the Queue resource and the Enqueue TwiML verb to place the caller on hold while the outbound call to you is made. Note: You could also use the Conference verb instead of Enqueue for potentially more options, simply by replacing Enqueue with Conference in the TwiML.
- To get started, follow this guide to set up your free Twilio account, get a phone number, and obtain your API SID and Token: https://www.twilio.com/docs/voice/quickstart/php
- Remember to configure the webhook for your Twilio phone number to point to your
step1.xmlfile (or select the appropriate TwiMLBin URL if using that).
Deployment Suggestion:
Setting up a dedicated web server isn’t strictly necessary. You can leverage Twilio’s own hosting features:
- Use Twilio TwiMLBins to host your XML files (like
step1.xml). Let Twilio handle the file hosting for you. - Use Twilio Functions for your server-side logic (converting the PHP logic to Javascript). The IVR Menu example in the Twilio documentation is a good starting blueprint for this.
I would strongly suggest using TwiMLBins for hosting XML files and, if you are capable, utilizing Twilio Functions for the server-side code to simplify your deployment.
Complete Business Start-up
Helping Native West Launch and Grow with Comprehensive Tech Solutions
We provided a wide array of technical solutions to help Native West successfully start their business and establish a strong digital presence. Our services included IP Phone Management, a custom Bidding System, and not only designing their website but also optimizing it to rank at the top of search engines.
Website Design
IT Services was responsible for both the design and development of the main Native West website.


SEO
Achieving Additional Site Links in Search Results
The term “Native West” presented a significant challenge for search engine optimization initially, as it was heavily dominated by content related to Native American topics. However, through proper site structure optimization and targeted SEO strategies, we quickly achieved the top spot in search engine results. Furthermore, their listing displayed with valuable additional site links, giving them increased visibility and click-through potential.
Phone System
Managed Phone System
We implemented a fully managed IP Phone System for Native West. This provided them with complete control and flexibility to customize call flow, directing calls efficiently to field agents, specific departments, or voicemail as needed.
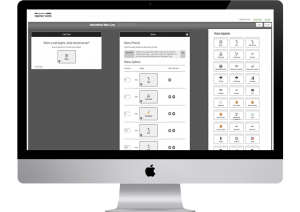
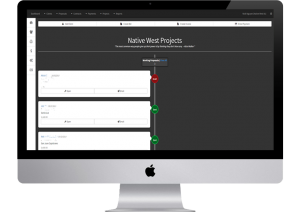
Management Platform
Bidding and Contract System
We developed a custom Management Platform that serves as the company’s operational backbone. This system is responsible for coordinating and connecting various departments – including Sales, Construction, Accounting, and Management – throughout the many complex stages of landscape construction projects, from initial bidding to final accounting.
Want more control over your company?
Schedule a free phone consultation to discuss how our solutions can help you streamline operations and gain greater control.






